
User Interface
Security Settings – Control Panel
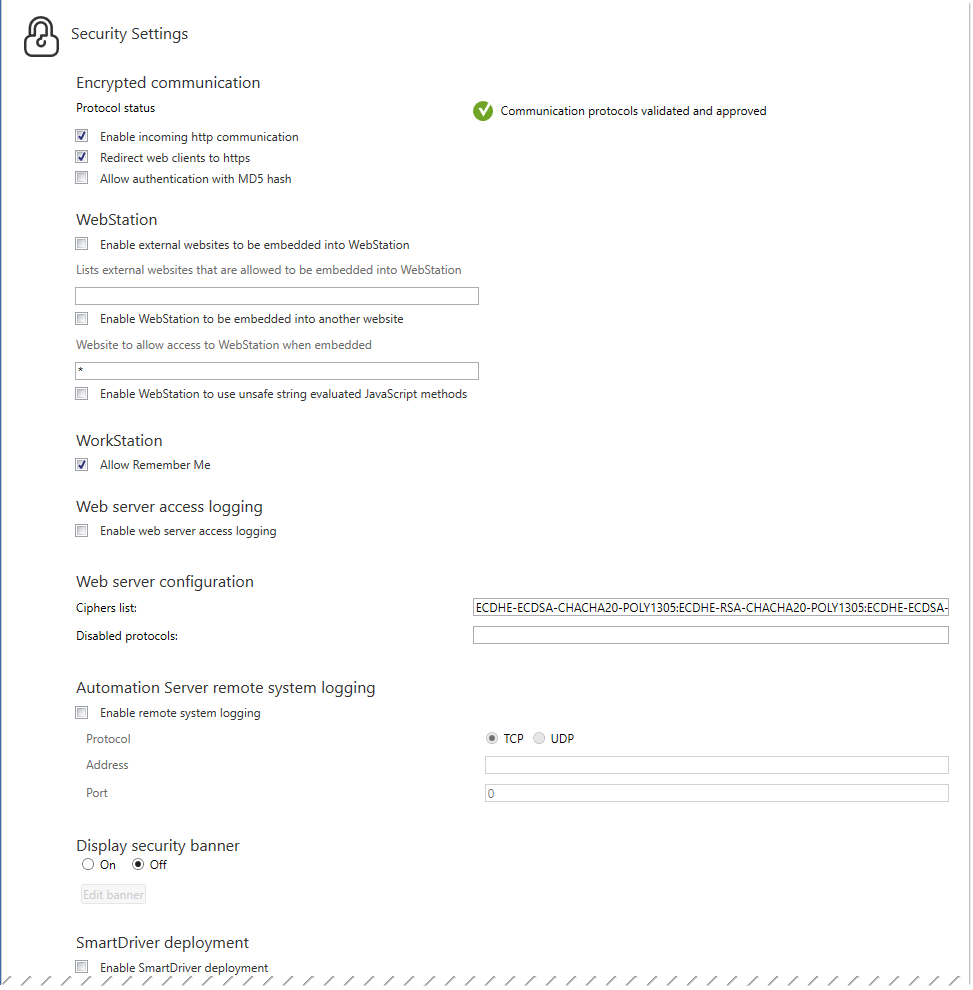
Use the Security Manager options on Control Panel to increase the security of your system.
|
Component |
Description |
|
Protocol Status |
Displays validation and approval of the protocols.


|
|
Enable incoming http communication |
Select to enable or disable incoming HTTP communication. For more information, see Encrypted Communication . |
|
Redirect web clients to https |
Select to redirect web clients to HTTPS. For more information, see Encrypted Communication . |
|
Allow authentication with MD5 hash |
Select to allow authentication with MD5 hash. For more information, see Encrypted Communication . |
|
Enable external content to be embedded in WebStation |
Enabling external websites to be embedded into WebStation lowers the security significantly. Do not enable external websites to be embedded into WebStation if you do not understand the security implications. For more information, see HTML Utilities . |
|
Lists external websites to be embedded into WebStation |
This setting is for internal R&D use only. The setting does not affect WebStation. |
|
Enable WebStation to be embedded in another site |
Select if you want WebStation to be embedded in another web site. For more information, see Security Configuration in WebStation . |
|
Website to allow access to WebStation when embedded |
This setting is for internal R&D use only. The setting does not affect WebStation. |
|
Enable WebStation to use unsafe string evaluated JavaScript methods like 'eval' |
Select if you have graphics written in older versions of EBO that cannot be displayed in 3.0 or later. For more information, see Cannot Open Graphics in WebStation . |
|
Enable web server access logging |
Select to log all web server HTTP access to the Enterprise Server or to the Enterprise Central. For more information, see Web Server Access Logging . |
|
Cipher list |
The cipher list consists of one or more cipher strings separated by colons. The names of the known ciphers may differ depending on which OpenSSL version the server was built to use. |
|
Disabled protocols |
Enter the protocol you want to disable. Separate the protocols with comma. Valid protocol names are tlsv1, tlsv1_1, tlsv1_2 and tlsv1_3. For more information, see Configuring SSL Communication Security Settings . |
|
Enable remote system logging |
Select to log all log on attempts on an automation server. For more information, see Field Server Remote System Logging . |
|
Protocol |
Select the protocol to use when sending log on attempts on the automation server. For more information, see Field Server Remote System Logging . |
|
Address |
Type the IP address to the server that is logging the log on attempts on the automation server. For more information, see Field Server Remote System Logging . |
|
Port |
Type the port number used by the server that is logging the log on attempts on the automation server. For more information, see Field Server Remote System Logging . |
|
Certificates |
Click to open the Certificates manager. For more information, see Certificates . |
|
Display Security Banner |
Select On to display a security banner at log on. For more information, see Security Banner . |
|
Password policy |
Click to open the Password policy dialog box where you configure the password policy. For more information, see Password Policy . |
|
Edit Banner |
Click to open the Edit Banner dialog box to edit the security banner. For more information, see Edit Banner – Dialog Box . |
|
SSH Console Lockout after |
Select the time when the SSH lockout is released. |
|
Connect Agent Settings |
Click to open the Connect Agent Settings dialog box where you configure the transfer of system information and crash information of the EcoStruxure BMS servers. For more information, see Configuring Connect Agent Settings . |
|
Enable SmartDriver deployment |
Select Enable SmartDriver deployment to make it possible to deploy new SmartDriver drivers. This option does not affect already deployed SmartDriver drivers. After the deployment, you can clear the option to prevent new SmartDriver drivers from being deployed. For more information, see SmartDrivers Overview . |
|
Restrict root permission to logged in server |
Select to restrict root permissions, i.e. ”/”, to the logged on server and its children servers. |
|
Enable federated authentication |
Select to enable federated authentication. For more information, see Federated Authentication . |
|
Invalid certificate settings for server to server communication |
Select Generate alarm to trigger an alarm if the server communication certificate is invalid. Select Block traffic to block traffic if the server communication certificate is invalid. |
 Encrypted Communication
Encrypted Communication
 Field Server Remote System Logging
Field Server Remote System Logging
 Certificates
Certificates
 Security Configuration in WebStation
Security Configuration in WebStation
 Cannot Open Graphics in WebStation
Cannot Open Graphics in WebStation
 Password Policy
Password Policy
 Web Server Access Logging
Web Server Access Logging
 Security Banner
Security Banner
 Configuring Connect Agent Settings
Configuring Connect Agent Settings
 Configuring SSL Communication Security Settings
Configuring SSL Communication Security Settings
 Edit Banner – Dialog Box
Edit Banner – Dialog Box
 SmartDrivers Overview
SmartDrivers Overview
 Federated Authentication
Federated Authentication