Log on to rate and give feedback
1
2
3
4
5
Log on to rate
0

Ratgeber
Produkte:
AS-B, AS-P, Project Configuration Tool
Funktionen:
Lokalisierung
Produktversion:
3.3, 2022
23.07.2021
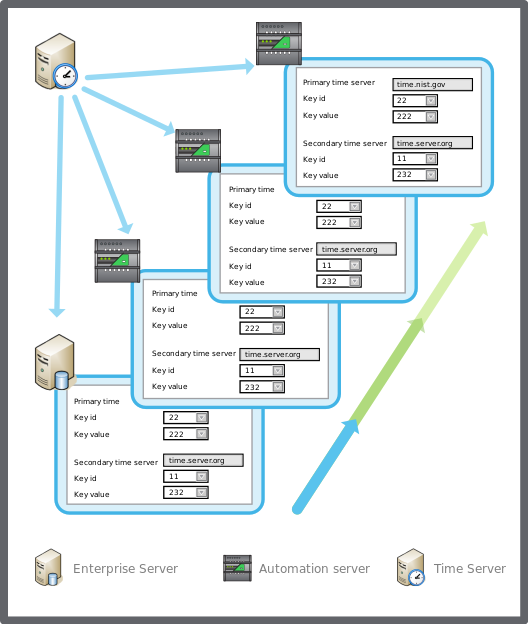
Synchronizing the Automation Server Clock
You configure the automation server to synchronize its clock with a network time server.
To synchronize the Automation server clock
In WorkStation, in the System Tree pane, select the automation BMS server you want to configure.
Click the Control Panel tab.
Click Network time and time zones .
In the automation server Date & time view, select Network time synchronization .
In the Primary time server box, type the address to the primary time server that you want to synchronize the automation server clock with.
In the Secondary time server box, type the address to the time server that you want to synchronize the automation server clock with if the primary time server is not available.
Click the Save button
.action_zoom_plus_stroke 
 Network Time
Network Time
 Time and Time Zone Configuration in Automation Server
Time and Time Zone Configuration in Automation Server
 Automation Server – Date & Time View
Automation Server – Date & Time View
 Manually Changing the Automation Server Time and Date
Manually Changing the Automation Server Time and Date
 Changing the Time Zone of an EcoStruxure BMS Server
Changing the Time Zone of an EcoStruxure BMS Server
 Creating a Custom Time Zone of an EcoStruxure BMS Server
Creating a Custom Time Zone of an EcoStruxure BMS Server