
Concept
Device Administrator Certificate Workflow
Use this workflow to create a trusted chain between Device Administrator and field server using a self-signed certificate.
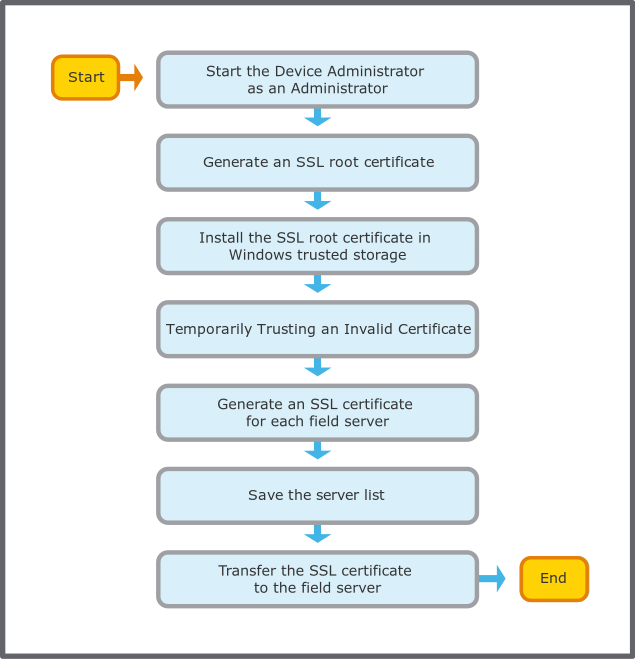
You need to be an administrator to install the certificate in Windows trusted storage. Refer to Windows for information on how to run a program as administrator.
Generate the SSL root certificate that is to be installed in Windows.
For more information, see Generating an SSL Root Certificate Using Device Administrator .
Install the SSL root certificate in Windows trusted storage.
For more information, see Installing an SSL Root Certificate to Windows Trusted Root Certificate Storage Using Device Administrator .
Trust the invalid certificate so that Device Administrator can tranfer the certificate to the field server.
For more information, see Temporarily Trusting an Invalid Certificate .
Generate an SSL certificate for each field server.
For more information, see Generating an SSL Certificate for a Field Server Using Device Administrator .
If you have many field servers in the list, you can use the Manage SSL Certificate Template to add default values for every new SSL certificate you want to generate.
For more information, see Generating an SSL Certificate for a Field Server Using Device Administrator .
You save the list after you have generated the certificates for each field server. It is recommended that you save the list after that you have generated the certificate for each field server.
Transfer the SSL certificate to all field servers in the list. This must be done manually for each server.
For more information, see Transferring an SSL Certificate to a Field Server Using Device Administrator .
The certificates are included in the field server’s backup. You do not need to generate a new certificate if you restore a field server from a backup generated after the certificate was transferred to the field server if you retain the original root certificate.
 Certificates Managed using Device Administrator
Certificates Managed using Device Administrator
 Generating an SSL Root Certificate Using Device Administrator
Generating an SSL Root Certificate Using Device Administrator
 Installing an SSL Root Certificate to Windows Trusted Root Certificate Storage Using Device Administrator
Installing an SSL Root Certificate to Windows Trusted Root Certificate Storage Using Device Administrator
 Temporarily Trusting an Invalid Certificate
Temporarily Trusting an Invalid Certificate
 Generating an SSL Certificate for a Field Server Using Device Administrator
Generating an SSL Certificate for a Field Server Using Device Administrator
 Transferring an SSL Certificate to a Field Server Using Device Administrator
Transferring an SSL Certificate to a Field Server Using Device Administrator
 Generating an SSL Certificate for a Field Server Using Device Administrator
Generating an SSL Certificate for a Field Server Using Device Administrator